Traffic for Google, Apple, Facebook, Microsoft and other tech giants routed through Russia, experts believe it was an intentional BGP Hijacking. Last week a suspicious event routed traffic for major tech companies (i.e. Google, Facebook, Apple, and Microsoft) through a previously unknown Russian Internet provider. The event occurred on Wednesday, researchers who investigated it believe the traffic was intentionally hijacked.
The incident involved the Internet’s Border Gateway Protocol that is used to route traffic among Internet backbones, ISPs, and other large networks.
https://twitter.com/bgpmon/status/940724787311022080
A similar incident occurred eight months when a huge amount of traffic belonging to MasterCard, Visa, and more than two dozen other financial services was briefly routed through a telecom operator controlled by the Russian Government.
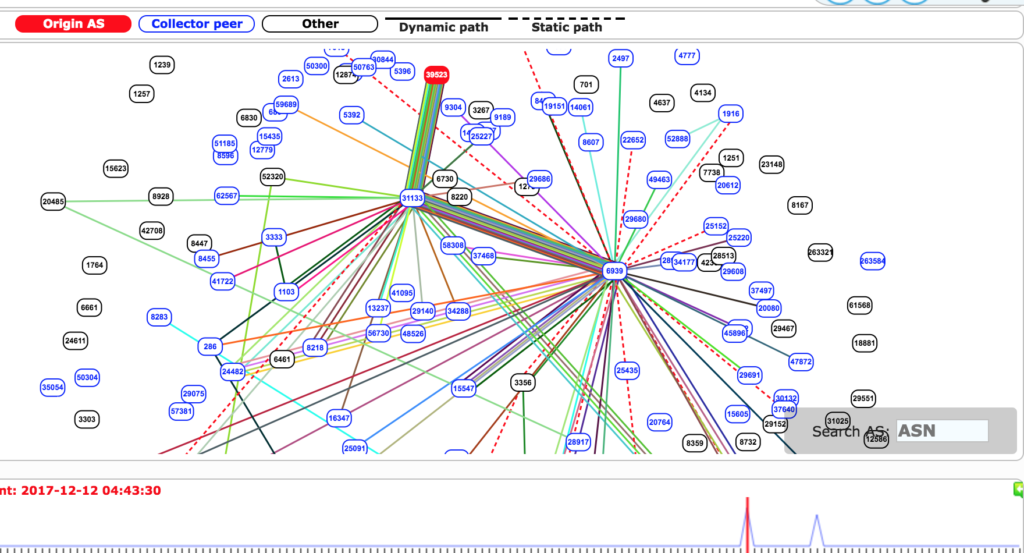
“Early this morning (UTC) our systems detected a suspicious event where many prefixes for high profile destinations were being announced by an unused Russian Autonomous System. Starting at 04:43 (UTC) 80 prefixes normally announced by organizations such Google, Apple, Facebook, Microsoft, Twitch, NTT Communications and Riot Games were now detected in the global BGP routing tables with an Origin AS of 39523 (DV-LINK-AS), out of Russia.” states a blog post published by Internet monitoring service BGPMon. “Looking at timeline we can see two event windows of about three minutes each. The first one started at 04:43 UTC and ended at around 04:46 UTC. The second event started 07:07 UTC and finished at 07:10 UTC. Even though these events were relatively short lived, they were significant because it was picked up by a large number of peers and because of several new more specific prefixes that are not normally seen on the Internet. So let’s dig a little deeper. “
BGPMon observed two distinct events for a total of six minutes that affected 80 separate address blocks.
Another monitoring service, Qrator Labs, stated the event lasted for two hours during which the number of hijacked address blocks varied from 40 to 80.
BGPMon experts consider the incident as suspicious for the following reasons:
- The rerouted traffic belonged to big tech companies.
- Hijacked IP addresses belong to small and specific blocks that aren’t’ normally seen on the Internet.
“What makes this incident suspicious is the prefixes that were affected are all high profile destinations, as well as several more specific prefixes that aren’t normally seen on the Internet. This means that this isn’t a simple leak, but someone is intentionally inserting these more specific prefixes, possibly with the intent the attract traffic.” continues the analysis from BGPMon.
The BGP hijacking was caused by an autonomous system located in Russia that added entries to BGP tables claiming it was the legitimate origin of the 80 affected prefixes. This assertion caused large amounts of traffic sent to and received by the affected companies to pass through the Russian AS 39523 before being routed to its final destination.
Below the list of ISPs that picked up the new route:
- xx 6939 31133 39523 (path via Hurricane Electric)
- xx 6461 31133 39523 (path via Zayo)
- xx 2603 31133 39523 (path via Nordunet)
- xx 4637 31133 39523 (path via Telstra)
AS39523 is a previously unused autonomous system that hasn’t been active in years, but he made the headlines in August when it was involved in another BGP incident that involved Google.
“Whatever caused the incident today, it’s another clear example of how easy it is to re-route traffic for 3rd parties, intentionally or by accident. It also is a good reminder for every major ISP to filter customers. ” concluded BGPMon.
“This hijack highlights a common problem that arises due to lack of route filtering. We can blame AS39523 for the accident, but without proper filters at the intermediate transit providers boundaries we are doomed to see similar incidents again and again. We’d like to encourage all networks involved in this incident to review their route filtering strategy, and at the very least implement prefix-based BGP filters on all interconnections towards their customers.” concluded Qrator Labs.