Identity theft is hard enough. That’s why we keep working to make recovering from it easier. It’s also why we’re happy to let you know about an innovative project by the FTC and IRS that lets people report tax-related identity theft to the IRS online, using the FTC’s IdentityTheft.gov website to file IRS Form 14039.
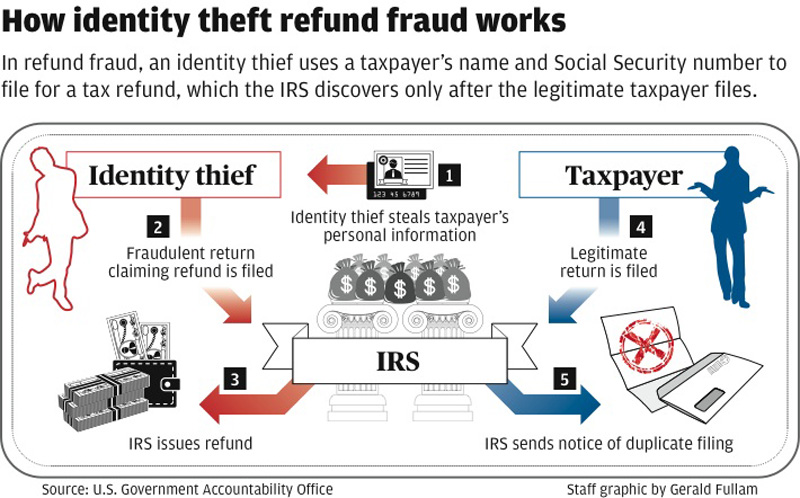
Tax-related identity theft happens when someone uses your stolen Social Security number (SSN) to file a tax return and claim your refund. You might find out about it when you try to e-file — only to find that someone else already has submitted a return — or when the IRS sends you a letter saying it has identified a suspicious tax return that used your SSN. That’s when you’ll need to file an IRS Identity Theft Affidavit (IRS Form 14039), so that the IRS can begin resolving your case.
Now, you can report to the IRS through IdentityTheft.gov. It’s the only place you can submit your IRS Form 14039 electronically. Here’s how it works: IdentityTheft.gov will first ask you questions to collect the information the IRS needs, then use your information to populate the Form 14039 and let you review it. Once you’re satisfied, you can submit the Form 14039 to the IRS through IdentityTheft.gov. Download a copy for your own records, too. About 30 days later, the IRS will send you a letter confirming it received the information.
While you’re at IdentityTheft.gov, you’ll also get help making an identity theft recovery plan, with guidance including how to place a fraud alert on your credit files, check your credit reports, and take other steps to stop the identity theft from harming other of your accounts. IdentityTheft.gov also will help you resolve other identity theft problems.
Remember, though — filing the Affidavit doesn’t eliminate the need to pay your taxes. If you couldn’t e-file your tax return, you’ll still need to mail it to the IRS and pay any taxes you owe.